Contents
JRC Tech Seminar Vol.5
Hello everyone, do you like our last blog about Cell Search and the System Information of the Cell? In this part, we will explain the procedure of Random Access in detail, hope you will like it!
After the UE and eNB have synchronized the DL, the UE moves to the random access procedure. Random access is performed in the following steps.
Msg1: Random access Preamble
To synchronize ULs, the UE sends a preamble.
Msg2: Random access Response
Based on the timing when the preamble is received, the eNB sends a message to the UE to adjust the UL timing. At the same time, the UE allocates resources to be used on the RRC connection.
Msg3: RRC Connection Request
The UE transmits the RRC connection request and UEID using the UL-SCH.
Msg4: RRC connection Setup (Contention Resolution)
The eNB sends a message of the RRC connection successful.
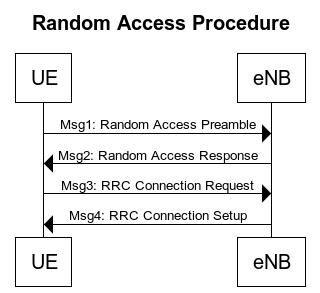
Random Access Overview
Msg1: Random Access Preamble
After the DL is synchronized, the UE sends a preamble to the eNB. This is to inform the eNB of the UE's existence and to allow the eNB to perform delay estimation between the UE and the eNB.
The preamble is transmitted via PRACH. eNB will inform the resources to be transmitted using PRACH by means of SIB2. Within a cell, there are 64 available preambles, and the UE chooses one of them to send a random access preamble to the eNB. There are two types of preambles: contention-free based and contention-based. The contention-free-based (NCB) preambles are used for HO, and the preambles are reserved in advance for easy attachment.
As shown in the figure below, when the eNB detects a preamble, it derives the RA-RNTI from the timing of the preamble's transmission. In the case of the following figure, RARNTI1 was derived from Preamble1. If the preamble is sent at the same time, the RA-RNTI will have the same value. This RA-RNTI is the random access identifier.
When a preamble is sent from different UEs, one preamble is decoded and prepared to send Msg2. In the following figure, preamble 1 of UE-B has not been received.
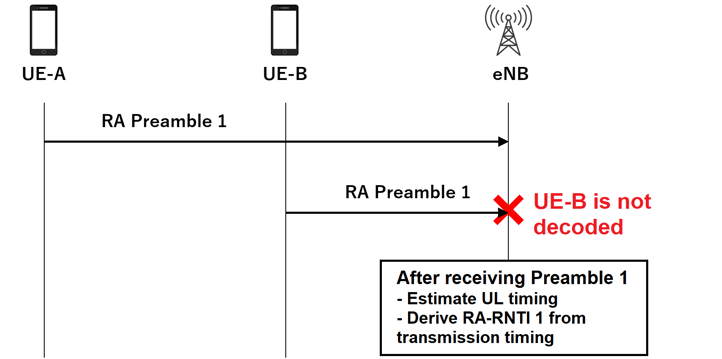 Details of Msg1
Details of Msg1
- Structure of Preamble
The preamble consists of the following two parts
・Preamble sequence
・Cyclic prefix
A guard time is provided when sending the preamble. The reason for this is that, although DL synchronization could be achieved in cell search, UL synchronization has not been established, and the position of the UE in the cell is not identified.
The random access preamble is made by a cyclic-shifted Zadoff-Chu sequence.
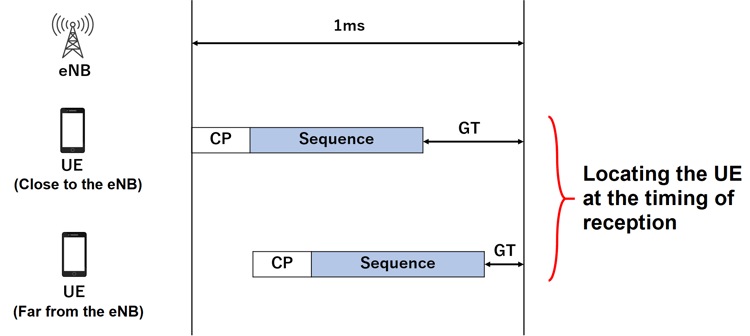 Preamble Transmission at UEs with Different Distances
Preamble Transmission at UEs with Different Distances
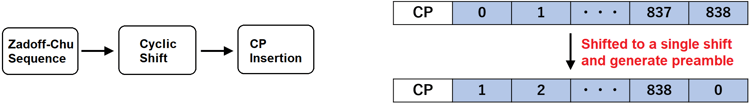 Preamble Generation
Preamble Generation
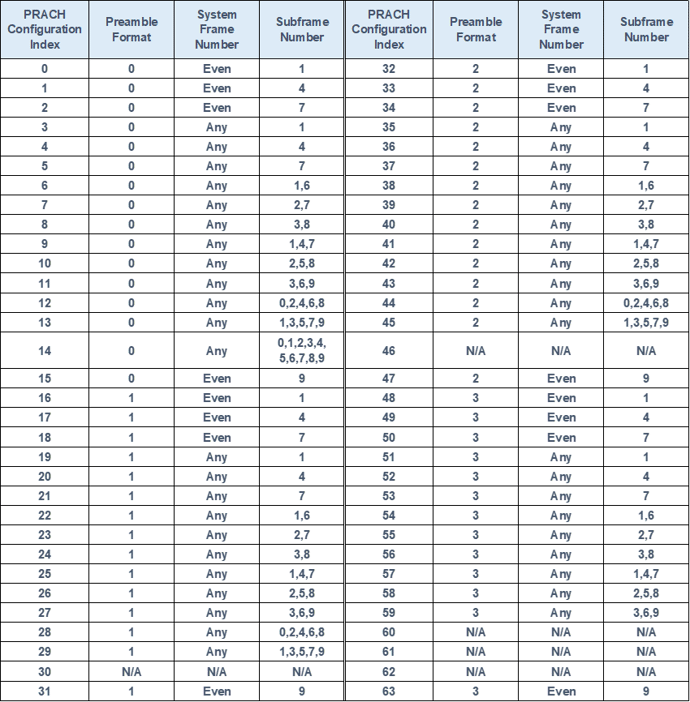
There are four different preamble formats, the cell radius also differs accordingly.
Feature: The larger the PRACH Configuration Index of the same format, the more resources are available for RA.
→ Opportunities increase and attachment becomes easier. But throughput degrades.
| LTE PRACH Preamble Format | CP Length | Sequence Length | Guard Time | Total Length | Guard Time equiv. dits. | Typical Max. Cell Range |
| 0 | 0.10ms | 0.8ms | 0.10ms | 1ms | 30km | 15km |
| 1 | 0.68ms | 0.8ms | 0.52ms | 2ms | 156km | 78km |
| 2 | 0.2ms | 1.6ms |
0.2ms |
2ms | 60km | 30km |
| 3 | 0.68ms | 1.6ms | 0.72ms | 3ms | 216km | 108km |
 Details of Preamble Format
Details of Preamble Format
Msg2: Random Access Response
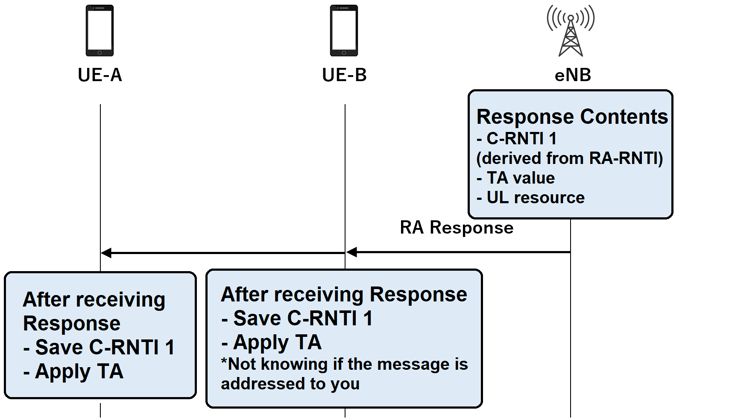
The eNB uses the RA-RNTI to calculate the C-RNTI, calculate the TA value from the UL timing, and allocate resources for the UE. The C-RNTI is used to identify the UE in subsequent messages. UE will save the C-RNTI after receiving the RA response.
The eNB also sends the following messages by DL-SCH. If the eNB receives random access requests from multiple UEs, it aggregates the response messages to each terminal into a single message and sends it.
・C-RNTI
・UL resource block
・TA value
In the figure below, the eNB is responding to the message of Preamble 1. Therefore, UE-B assumes that its own preamble has been decoded. After receiving Msg2, each UE prepares to send Msg3. So that the C-RNTI in Msg2 will be saved.
 Details of Msg2
Details of Msg2
Msg3: RRC Connection Request
At the end of Msg2, UL synchronization is established, but the eNB is not aware of each UE, so Msg3 and Msg4 will resolve the contentious issue.
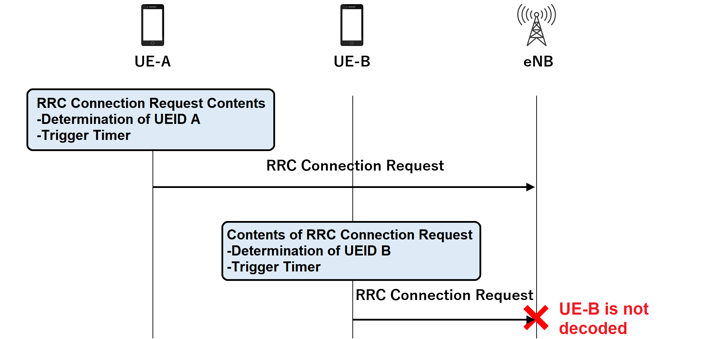
The UE uses the allocated resources to send an RRC connection request to the eNB, including a UEID randomly generated by the UE.
In the following figure, both UE-A and UE-B generate their own UEIDs and send Msg3. However, UE-B's Msg is not decoded here as well, since Msg1 was not decoded.
Details of Msg3
Msg4: RRC Connection Setup (Contention Resolution)
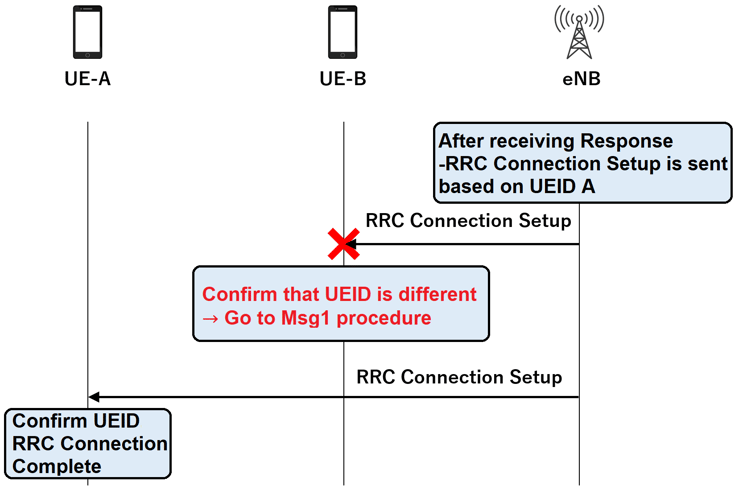
The eNB replies to the RRC connection request message. In this case, the reply is sent using a random number generated by the UE. If its own UEID is included in the message, it will recognize that the RRC connection has been completed.
After UE-B receives Msg4 in the following figure, it can be confirmed that the random access is not successful because the UEID is different from the one sent by UE-B itself. UE-B then needs to start over from Msg1. Also, if the message does not come within the time of the trigger timer sent in Msg3, the random access will also be redone.
 Details of Msg4
Details of Msg4
For further information about Private LTE, please check out our other blogs and use cases. If you have any questions, please do not hesitate to contact us.












